Hey guys, Rocky here! 🔓🚨
Welcome to Day 16 of the Daily Web Hacking series! Today, we’re tackling Security Misconfiguration—the silent killer lurking in default settings, debug modes, and forgotten open doors. Imagine leaving your house keys under the doormat or your car unlocked in a parking lot. That’s what security misconfiguration looks like in the digital world. Let’s dive into how hackers exploit these oversights and how to lock things down!
—
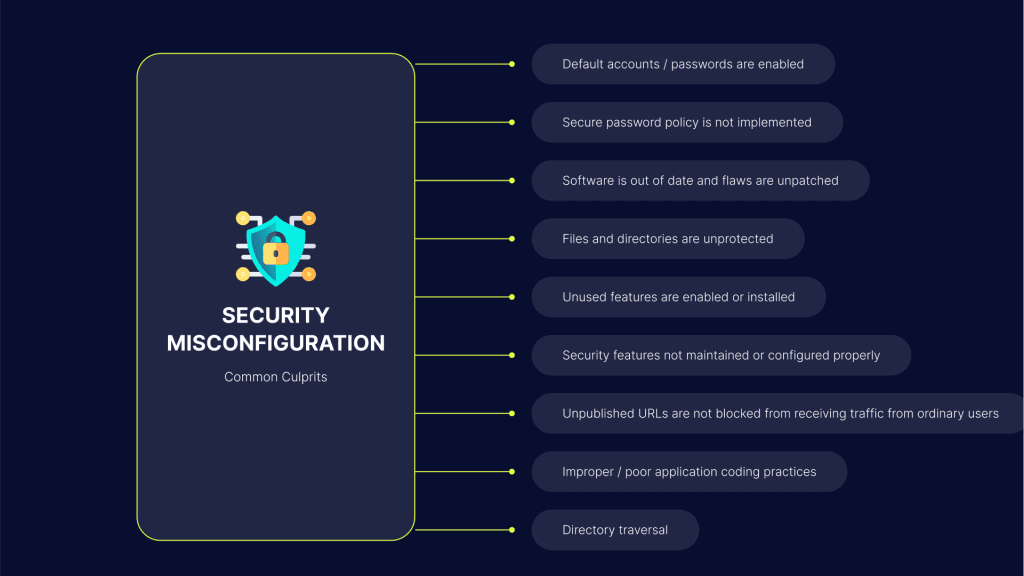
What is Security Misconfiguration?
Security misconfiguration occurs when systems, applications, or services are deployed with insecure settings, unnecessary features, or default configurations. These oversights create easy entry points for attackers, often requiring no advanced exploits—just awareness of where to look.
Why it’s dangerous:
- #5 in the OWASP Top 10 (2021).
- Found in 40% of breaches (Verizon DBIR, 2023).
- Low effort, high reward: Attackers exploit laziness, not complexity.
—
Common Types of Security Misconfigurations
1. Default Credentials & Settings
- Example: Admin panels left with factory defaults (
admin:admin).
- Tools:
- Shodan: Search for devices using default logins.
- Hydra: Brute-force default passwords.
Real-World Exploit:
In 2021, attackers breached a hospital’s HVAC system via admin:admin on an exposed IoT device.
—
2. Debug Mode Enabled in Production
Example: Flask/Django apps running with DEBUG=True, exposing stack traces and code snippets.
Exploit: Trigger errors to leak secrets:
GET /api/user?id=INVALID_INPUT
→ Response:
ValueError: Invalid user ID at /app/views.py:42
SECRET_KEY = "s3cr3t_k3y_123" # Leaked!
—
3. Open Directories & File Permissions
- Example: Exposed
/backups, /config, or /logs directories.
- Tools:
- DirBuster: Brute-force directory listings.
- Google Dorking:
site:example.com intitle:"index of /" "config".
Case Study:
A tech startup left their AWS credentials in s3://company-config/config.yml, leading to a $500K cloud bill hijack.
—
4. Unnecessary Services & Ports
Example: Redis, MySQL, or FTP running on public ports.
Exploit: Use nmap to find open ports:
nmap -sV example.com
PORT SERVICE VERSION
6379/tcp redis Redis 6.0.0
→ Attackers exploit unauthenticated Redis to gain shell access.
—
5. Verbose Error Messages
Example: SQL errors revealing database structure:
ERROR: Table 'users' does not exist
→ Attackers map the database for SQLi.
—
6. Insecure Security Headers
- Example: Missing
Content-Security-Policy (CSP) or X-XSS-Protection.
- Impact: Allows XSS, clickjacking, and MIME sniffing.
—
Step-by-Step Exploitation
Scenario: Hacking an Exposed Admin Panel
- Find the Panel: Use Shodan to search
title:"Admin Login" http.component:React.
- Default Credentials: Try
admin:admin, admin:password, or check vendor docs.
- Access Sensitive Data:
- Download user databases.
- Modify system configurations (e.g., disable firewalls).
—
Scenario: Exploiting Debug Mode in a Web App
- Trigger an Error: Submit invalid input (e.g.,
GET /profile?id=INVALID).
- Leak Secrets: Extract API keys, database credentials, or internal IPs from stack traces.
- Escalate Access: Use leaked credentials to pivot into internal networks.
—
Real-World Disasters
- Equifax (2017): A misconfigured Apache Struts server led to a 147M-record breach.
- Microsoft (2020): Exposed Azure Blob Storage leaked 250M customer support logs.
- Facebook (2019): Open AWS S3 buckets exposed 540M user records.
—
Tools for Finding Misconfigurations
1. Automated Scanners
- OWASP ZAP: Crawls sites for open directories, debug modes, and insecure headers.
- Nessus: Detects default credentials, unnecessary ports, and vulnerable services.
2. Manual Recon Tools
- Shodan: Find devices with default settings (
default password country:US).
- DirSearch: Fast directory brute-forcing.
3. Cloud-Specific Tools
- AWS Inspector: Scans for S3 bucket misconfigurations and open security groups.
- Prowler: Audits AWS/GCP/Azure environments for compliance gaps.
—
Defending Against Misconfigurations
1. Harden Defaults
- Change default credentials immediately after deployment.
- Disable unused services (e.g., FTP, Telnet).
2. Embrace Least Privilege
Restrict file/directory permissions:
chmod 600 /app/config.yml # Only owner can read/write
Use IAM roles in cloud environments (e.g., AWS ReadOnly access).
3. Secure Debugging & Logging
Disable debug mode in production:
# Django settings.py
DEBUG = False
Sanitize logs: Remove secrets and PII before storage.
4. Audit Security Headers
5. Regular Scans & Audits
- Schedule weekly vulnerability scans.
- Conduct penetration tests to uncover hidden flaws.
—
The Cost of Complacency
- Financial: Fines (GDPR, CCPA), breach cleanup costs, lost revenue.
- Reputational: Customer trust erosion, brand damage.
—
Final Thoughts
Security misconfigurations are the low-hanging fruit of cyberattacks. They don’t require genius hackers—just negligence. By adopting a paranoid mindset, automating checks, and auditing relentlessly, you can slam these open doors shut.
Next Up: Day 17: Vulnerable Components – When Outdated Libraries Own You
—
Rocky out! ✌️
—
P.S. If you’re enjoying this series, share it with your team! Let’s turn “We’ll fix it later” into “We secured it now.”
Discussion Question: What’s the wildest misconfiguration you’ve seen? I once found a publicly exposed Jenkins server with no password. 😅 Spill your stories below! 👇